
Dealership cybersecurity is more important than ever. In the past, hackers focused their efforts on large enterprises, but it’s becoming just as common for small businesses and individuals to be targeted. Now, there are new cybersecurity vulnerabilities that didn’t exist a few years ago.
Social engineering schemes directed at obtaining sensitive data have become the most expensive and fastest-growing form of cyberattacks. For hackers, your dealership is a gold mine of information – from customer addresses to finance and insurance information. Investing in the right cybersecurity methods will protect your dealership’s reputation and be more cost-effective in the long run.
With help from Roger A. Grimes, Data-Driven Defense Evangelist at Knowbe4, this article outlines the most common cybersecurity threats to your dealership, the motivations behind why hackers hack, how they hack, and what your dealership can do to minimize its risk of cyberattacks.
Table of Contents:
- What is Cybersecurity?
- Who Do Cyberattacks Target?
- Why Do Hackers Hack?
- How Do Hackers Hack?
- Dealership Cybersecurity Best Practices
What is Cybersecurity?
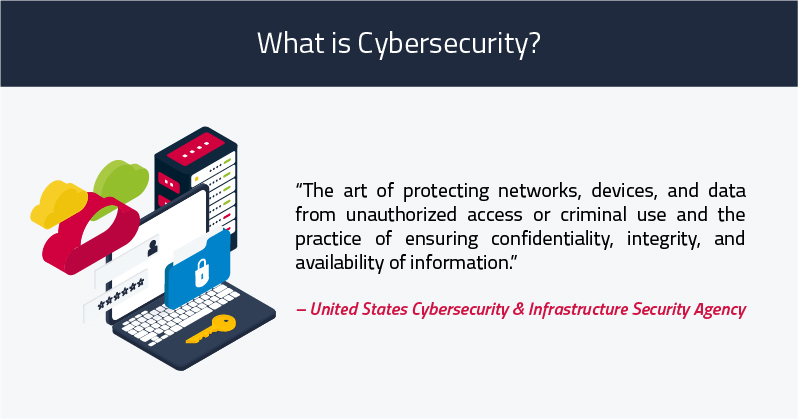
The United States Cybersecurity & Infrastructure Security Agency defines cybersecurity as:
The art of protecting networks, devices, and data from unauthorized access or criminal use and the practice of ensuring confidentiality, integrity, and availability of information.
Typically, cybersecurity is about understanding the behavior of attackers and identifying their behavioral cues to stop cyberattacks. This means understanding attackers’ motivations and their methods and strategies for evading security measures and deceiving victims. By understanding their techniques, organizations can implement the necessary security solutions to prevent cyberattacks.
Types of Cybersecurity Threats
There are different types of cybersecurity threats to your dealership including malware, ransomware, phishing/social engineering, insider threats, and distributed denial of service (DDoS) attacks.
Malware
Malicious software such as worms, viruses, Trojan horses, and spyware, that grant illegal access or harm a computer are referred to as “malware.” Malware attacks try to avoid common detection techniques, like antivirus software, that usually check for harmful files.
Ransomware
Ransomware is also considered a type of malware. Hackers use ransomware to encrypt or lock down files, data, or systems and demand a ransom payment from the victim of the cyberattack to unlock their information. The data is erased, destroyed, or made public if the ransom isn’t paid.
Phishing
Phishing is a method of social engineering that tricks users into giving out sensitive information, such as their login information or credit card numbers. They usually appear as emails or text messages from a legitimate organization that asks for personal information by clicking on a link or downloading a file. However, that link or file contains malware.
Insider Threats
Insider threats are the result of current or former employees, business partners or anyone with access to a network in an organization, that misuses their access privilege to obtain insider information.
DDoS
Distributed denial of service (DDoS) attacks can bring down a server, website, or network by flooding it with traffic from several synchronized systems or devices known as a robot network or botnet.
Read Next: How Farm Equipment Dealers Use Software to Manage Their Business

Who Do Cyberattacks Target?
Cybersecurity risks exist in every industry, including dealerships.
Hackers will take advantage of any opportunity that will allow them to obtain valuable information from small businesses and large organizations. Ransomware attacks especially have been affecting more industries than ever, including local governments and non-profits with increasing threats to vital infrastructure, supply chains, and government websites.
Insights into data security clearly indicate that users are the weakest part of an organization’s cybersecurity. In the Thales’ 2022 Data Threat Report, 38% of organizations rank human error as the highest threat to organizational security. While it’s important for organizations to implement security measures, it’s even more important to train users to identify cyber threats, especially phishing and social engineering schemes.
As many as 85% of cybersecurity breaches have a human element with cyber attackers using a sense of urgency or credibility to make victims engage with malicious content. The tactics and behaviour of these attempts are usually consistent too, such as making the victim click a link or open an attachment.
Why Do Hackers Hack?

You might be wondering why hackers would ever want to go after your dealership – after all, why you?
However, the majority of cyberattacks are random and your business was simply a victim of opportunity. Hackers send out hundreds of millions of phishing emails every day. It just so happened that you or someone in your organization was tricked into clicking on the targeted link.
Cybercriminals will also go after specific targets, although this is less common. Targets are typically larger and more well-known institutions. For example, state and local governments are ransomware targets because they are under more pressure to pay ransom to restore the websites and programmes people depend on.
Financial Motivation
It’s no surprise that most dealership cybersecurity threats are financially motivated. Attackers will do whatever it takes to get money. For example, ransomware can help hackers steal an organization’s data allowing them to lock up files and obtain sensitive data, such as passwords, giving them access to bank accounts, credit cards, and a person’s identity.
Steal or Leak Information
Relatedly, hackers hack to steal and leak sensitive information. Their motivations can be politically charged. A hacker may look for information that will benefit their country or sow discontent in another country. Cyberattacks may also be the result of corporate espionage by a competitor who is looking to obtain protected information, such as trade or industry secrets and intellectual property.
Take Advantage of Computer Resources
Sometimes hackers just want to use your computer’s resources. All sorts of devices can be taken over by malware including webcams, modems, and even DVRs. Once taken over, the devices interact like “bots” and operate within bot networks. Hackers will resell those bot networks to someone else or use them to attack other organizations. For example, adware can redirect your computer resources by manipulating your browser or operating system to direct views towards a particular website.
Personal Objectives
Lastly, hackers have their own personal motivations for hacking that may or may not be malicious. For example, “hacktivists” may have philosophical differences with an organization and attempt to shut them down. They might also cause public embarrassment by doxxing (searching and releasing private information) political figures they disagree with.
Read Next: How Appling Motors Have Future-Proofed Their Data with Cloud Hosting
How Do Hackers Hack?
Hacking typically involves some type of automated malware, such as trojan horse programs or worms. They trick the user into clicking on a link or downloading an attachment that lets the malware get access to someone’s device or network.
Most attacks these days are hybrid attacks that involve malware and a human adversary. The malware obtains the initial access and lets the hacker know, or “dial home,” that it has obtained access to a device. The human adversary is then able to take over.
Attacker Workflow:
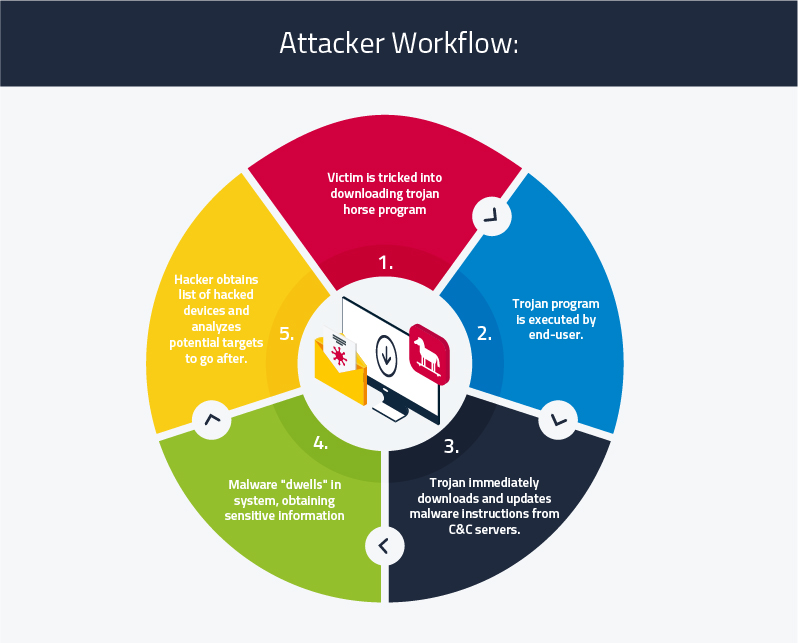
This is how most hacking occurs today:
- The victim is tricked (socially engineered) into downloading a trojan horse program. The trojan horse program is executed in some way by the end-user. It installs itself on the system, living through reboots and collecting passwords saved in browsers. The information is then uploaded to command-and-control servers (other people’s computers and network devices taken over by malware).
- After the trojan horse program is executed, it immediately downloads and updates additional malware and instructions from those command-and-control servers. The vast majority of malware that gets onto computer systems today can remain hidden for 8-12 months before it does damage. The typical user affected by malware doesn’t know it because it could be in their system for months.
- The malware “dwelling” in your system obtains financial statements, emails, and passwords from anyone on your network. The command & control centre gives hackers a list of all the systems they’ve broken into, allowing the hacker to come in and assess the information, analyse their targets, and decide which victims to go after.
Read Next: Five Keys to Understanding Your Dealership Network
Dealership Cybersecurity Best Practices
On average, there are 4,000 – 20,000+ new cyber threats a year or 11-55 new threats per day. The two most common ways that hackers get in are:
- Social engineering
- Unpatched software
Together, these make up 90% of most hacking attempts.
Social engineering is when a victim is tricked into downloading a file and running it. Phishing is the most common form of social engineering attack and can take place in several different ways. Typically, it involves some type of trick messaging. For example, you may get an email about fraudulent activity in your email account that requires you to click on a link to reset a password. However, if you hover over the link, it will look suspiciously long.
Social media is also becoming a more common spot for phishing attempts. Hackers can compromise your friends and family too. If they’re compromised, they can send you a link on social media telling you to watch a video, but instead you’re forced to download software to access the video. Malicious SMS messaging, or “smishing” might also trick you into clicking a link to get your login and password information.
Protecting Your Dealership Against Social Engineering
The best way to mitigate social engineering is by fighting the social engineer. This means training all your employees on how to spot scams and rogue URLs.

Most social engineering scams will have these 4 traits:
- The message arrives unexpectedly
- The sender is asking you to do something you’ve never done for that sender before
- The message includes a stressor event – e.g., it asks you to act NOW
- The request is malicious – performing it can harm your interests
If you do identify these attempts, the best course of action is to report it to your IT person who can investigate further. The more you and your coworkers are aware of suspicious URLs and can spot social engineering attempts, the more you’ll reinforce your dealership’s cybersecurity measures and prevent your business from being the victim of a cyberattack.
Use phishing-resistant Multi-Factor Authentication (MFA) where you can. Where you can’t, update passwords regularly and use unique, unguessable combinations for every website and service. A password manager or vault can help you save and keep track of different passwords. It’s also important to always patch internet-accessible software and to update your network consistently.
Read Next: 5 Benefits of Adopting Cloud Computing at Your Dealership
Safeguard Your Dealership with Cloud Hosting
If you are manually updating your software, it is easy for updates to be missed or postponed, making your dealership network more vulnerable to cyberattacks. Cloud hosting gives your dealership an added layer of cybersecurity. Your cloud provider will manage the IT infrastructure for you, ensuring that your network is always up to date, and eliminating the need for manual software updates and back-ups.
Your applications and data are also safeguarded by their security procedures, protecting your data and applications more securely than on-premises servers. Cloud providers also have fewer outages overall and are less vulnerable to ransomware attacks. In the event of a cyberattack or disaster, you can easily access and restore your data because of regular backups.
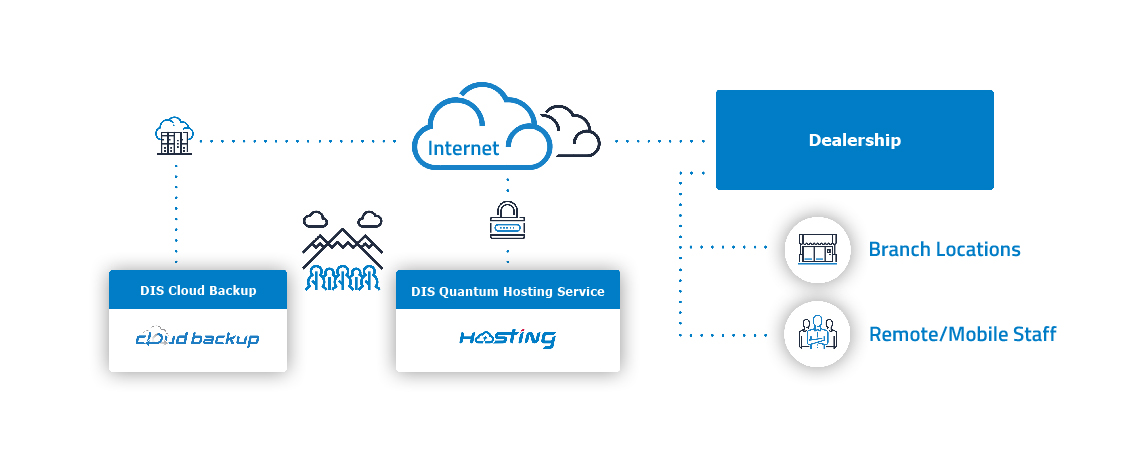
With DIS Cloud, your server is managed, maintained, and operated by DIS.

![Fixed Absorption: Your Dealership’s Recession Shield [Infographic]](https://www.discorp.com/wp-content/uploads/2025/04/Blog-prev-190x190.jpg)


